Impressive Tips About Can You Undo XOR
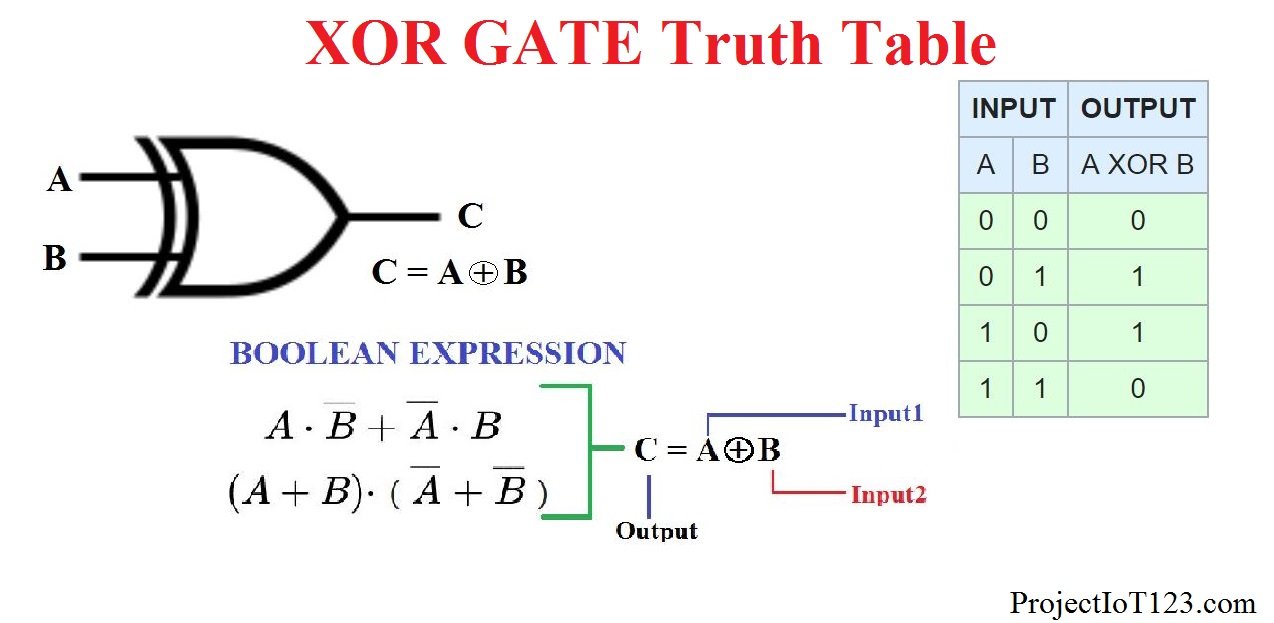
Diagram Of Xor Gate
Unlocking the Secrets of XOR
1. Understanding XOR
Ever stumbled upon XOR and thought, "What in the world is this?" Well, you're not alone! XOR, short for "exclusive OR," is a logical operation that's a cornerstone of computer science and cryptography. Simply put, it compares two bits (0 or 1). If the bits are different, the result is 1; if they're the same, the result is 0. Think of it like a quirky coin flip where only heads and tails win!
But how does this seemingly simple operation become so powerful? XOR's magic lies in its reversibility. This reversibility is what we mean by "undoing" it, which we'll dive into more deeply. It's the secret sauce behind many encryption algorithms and error-detection methods. Imagine you have a message you want to keep secret; XOR can help you scramble it up nicely, and then, like a magician revealing the trick, it can unscramble it just as easily.
To really get a grasp on XOR, think about it in terms of everyday situations. Imagine you have two light switches controlling one light. If both switches are in the same position (both up or both down), the light is off. If they're in different positions, the light is on. That's XOR in action! This kind of thinking can help make the whole thing less abstract and more relatable.
The beauty of XOR is that it's not just about the ones and zeros. It's about the logic and the principles that can be applied across many areas, from safeguarding your data to ensuring the integrity of transmitted information. So buckle up, as we're about to explore the fascinating world of XOR and find out if we can indeed undo its effects!

Bitwise XOR Operator In Java Programming Language YouTube
The Reversibility of XOR
2. How the XOR Operation is Undone
Here's the big question: Can you actually undo XOR? The short answer is a resounding YES! The real question is how. And the answer lies in a rather elegant property of XOR: applying the same XOR operation a second time with the same key restores the original data.
Let's break that down. Imagine you have a piece of information, say the number 5 (represented as 0101 in binary). You want to "encrypt" it using XOR with a "key," let's say the number 3 (0011 in binary). Performing the XOR operation, 0101 XOR 0011, gives you 0110 (which is the number 6). Now, to get back to the original number 5, you simply XOR 0110 with the same key, 0011. Voila! 0110 XOR 0011 = 0101, and you're back where you started.
This "undoing" process is what makes XOR so incredibly useful in various fields. It's like having a secret decoder ring where you can both scramble and unscramble messages with the same key. This isn't just theoretical, either. Many encryption algorithms rely on this property to securely transmit data across the internet.
Think of it like a seesaw. Applying the XOR operation is like pushing down on one side of the seesaw, changing the state. Applying the same operation again is like pushing down on the same side, which brings it back to its original position. It's a beautiful symmetry that makes XOR a true workhorse in the world of computing. Its actually so simple, it's almost magical!

Circuit Diagram Of Xor Gate Using Nand
Practical Applications of Undoing XOR
3. Real-World Scenarios Where XOR Shines
Okay, so we know you can undo XOR. But where does this magical ability actually come in handy? The possibilities are surprisingly broad! One major area is in data encryption. XOR is used in various encryption algorithms because of its simplicity and reversibility. It's a fast and efficient way to scramble data, and because it can be easily undone, it allows for secure communication.
Another crucial application is in error detection, particularly in RAID (Redundant Array of Independent Disks) systems. These systems use XOR to calculate parity bits, which are used to detect and correct errors in data storage. If one disk fails, the missing data can be reconstructed using the XOR of the remaining disks. This is a lifesaver for data centers and anyone who values their precious information.
Beyond these core applications, XOR also finds its way into graphics processing, image manipulation, and even simple tasks like toggling bits in hardware. It's a versatile tool that every programmer should have in their arsenal. The underlying principle is always the same: use XOR to change a state, and use XOR again with the same key to revert back.
Imagine a scenario where you have a security camera system. Using XOR, you can easily encrypt the video feed being transmitted, so even if someone intercepts it, they can't decipher it without the key. Or consider a program that manages user preferences; XOR can be used to quickly and efficiently toggle settings on and off, saving precious processing power.
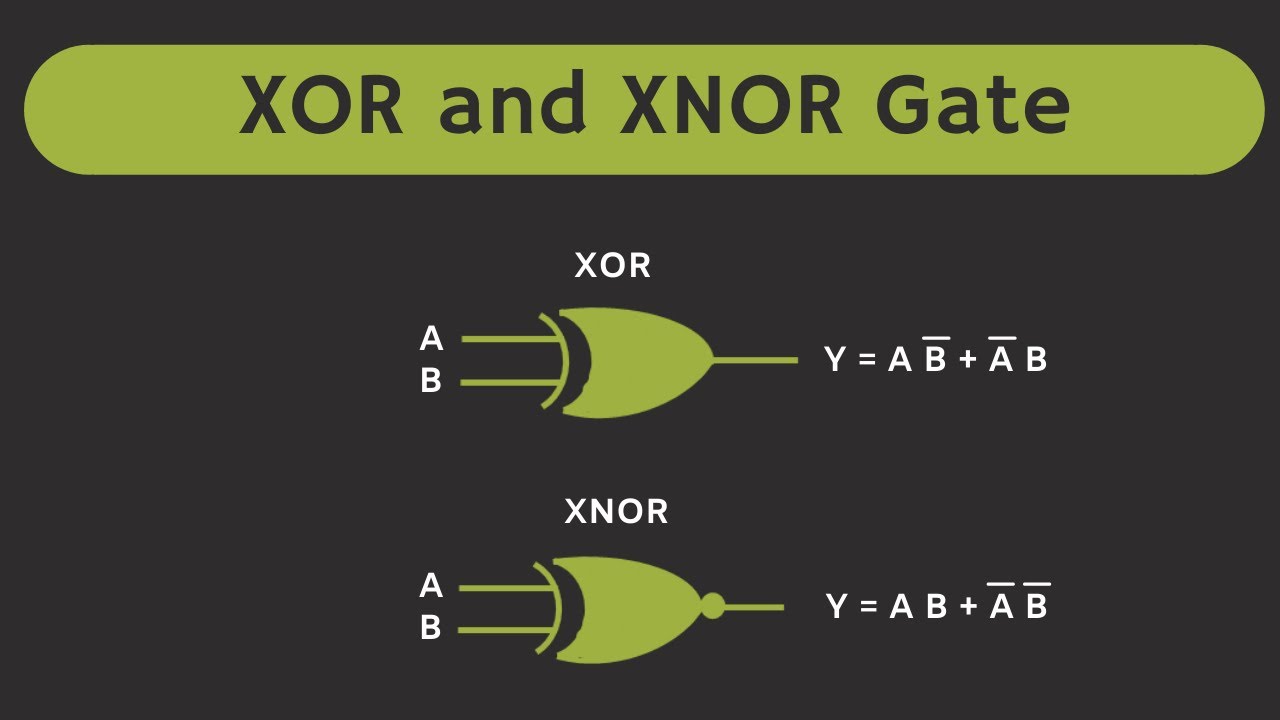
Limitations and Considerations When Using XOR
4. When XOR Might Not Be the Best Choice
While XOR is undeniably powerful and versatile, it's not a silver bullet. It has its limitations, and it's crucial to understand them to avoid potential pitfalls. The most significant limitation is its vulnerability to known-plaintext attacks. If an attacker knows both the original plaintext and the ciphertext (the XORed version), they can easily recover the key by simply XORing the two together.
This means that XOR, on its own, is generally not suitable for high-security applications. More sophisticated encryption algorithms, such as AES (Advanced Encryption Standard), are typically preferred for sensitive data. However, XOR can still be a valuable component in these more complex systems, often used in combination with other cryptographic techniques to enhance security.
Another consideration is the key management. The security of XOR encryption relies entirely on the secrecy of the key. If the key is compromised, the encryption is effectively broken. Therefore, it's essential to protect the key from unauthorized access and use secure methods for key exchange and storage. Think of the key as the actual secret you're trying to protect. If the key is simple or easy to guess, the whole thing can fall apart quickly.
Finally, remember that XOR is a symmetric encryption algorithm, meaning the same key is used for both encryption and decryption. This can create logistical challenges in environments where multiple parties need to communicate securely. Distributing and managing the key securely among all parties can be a complex and error-prone process. So, while XOR is great for some things, remember to pick the right tool for the right job!
Advanced XOR Techniques and Applications
5. Going Beyond Basic XOR Operations
Once you've mastered the basics of XOR, you can start exploring more advanced techniques and applications. One interesting area is the use of XOR linked lists, which offer a memory-efficient way to implement doubly linked lists. Instead of storing separate pointers for the next and previous nodes, an XOR linked list stores the XOR of the addresses of these nodes. This can save significant memory, especially in situations where memory is limited.
Another advanced technique is the use of XOR in cryptography for creating more robust encryption schemes. By combining XOR with other cryptographic operations, you can create algorithms that are more resistant to attacks than simple XOR encryption alone. These techniques often involve multiple rounds of XOR and other operations, making it much more difficult for attackers to decipher the ciphertext.
XOR also plays a crucial role in various hardware applications. For instance, it's used in memory controllers for error detection and correction, as well as in digital circuits for implementing logic gates. Its speed and simplicity make it an ideal choice for these performance-critical applications. So you can see XOR shows up even at the core level of how some hardware functions!
Exploring these advanced XOR techniques and applications can open up a whole new world of possibilities. It's a testament to the power and versatility of this simple yet elegant operation. From memory management to cryptography to hardware design, XOR continues to be a valuable tool for solving a wide range of problems.
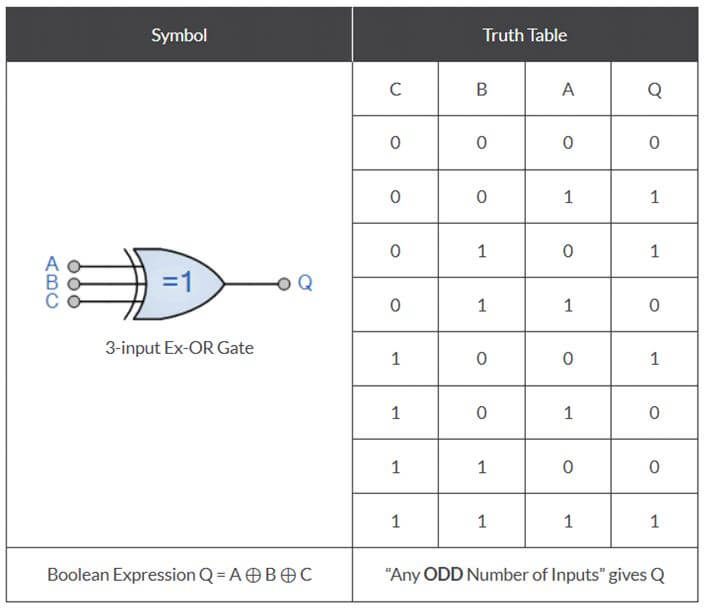
FAQ
6. Your Burning Questions Answered
Q: Is XOR encryption unbreakable?A: Nope! While XOR encryption is simple and fast, it's definitely not unbreakable, especially when used alone. If someone gets their hands on both the original, unencrypted data (plaintext) and the encrypted version (ciphertext), they can easily figure out the key. It's best used as part of a more complex encryption system or for situations where top-level security isn't a must.
Q: Can XOR be used with any type of data?A: Absolutely! XOR operates on bits (0s and 1s), so any data that can be represented in binary format (which is basically all data in computers) can be XORed. This includes numbers, text, images, and even video. The key is to understand how the data is represented in binary.
Q: Why is XOR used in RAID systems?A: RAID (Redundant Array of Independent Disks) systems use XOR for its error-correction properties. It helps to create parity data, which, in turn, means if one of the hard drives in the array fails and becomes unreadable, the lost data can be reconstructed using XOR operations on the remaining drives. It's like having a built-in backup plan for your data, and XOR is one of the reasons that is possible!